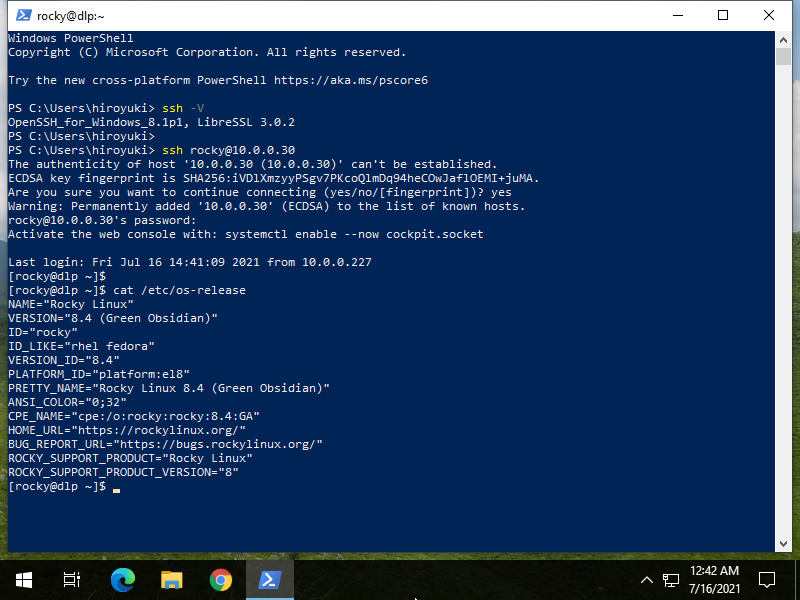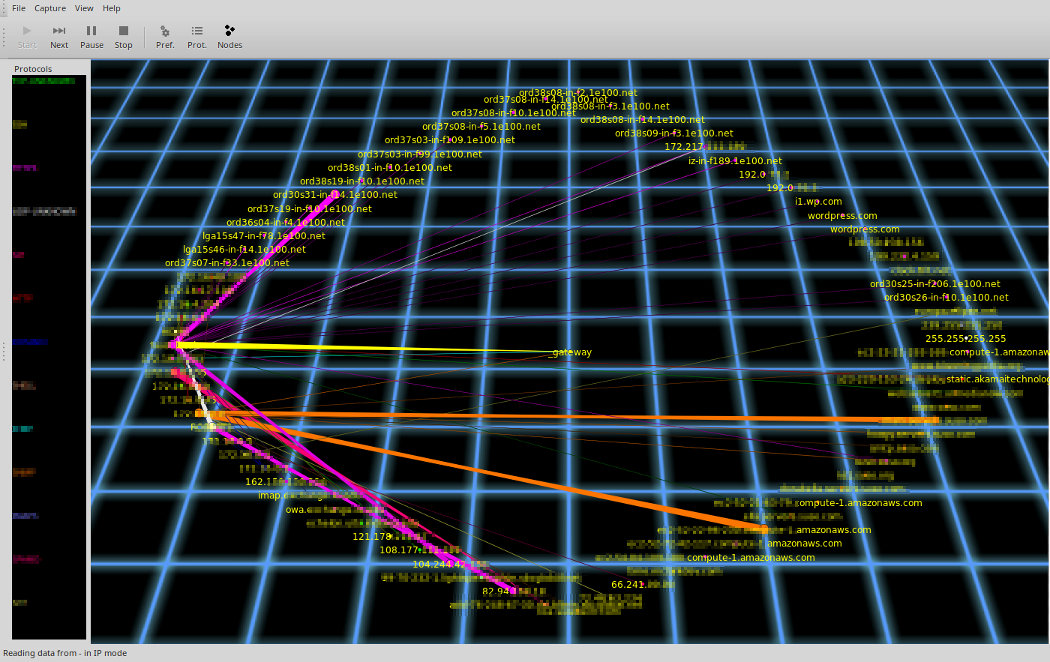
Command Line Magic on Twitter: "ssh root@192.168.0.1 tcpdump -n -i any -w- 'not \( port 22 and host 192.168.0.1 \)' |etherape -r- # Instant visualization of linux router traffic. Yes, root on

Stanley Milgram Quote: “Some system of authority is a requirement of all communal living, and it is only the man dwelling in isolation who is no...”

GitHub - RamonLucio/Born2beRoot: This project aims to introduce you to the wonderful world of virtualization.
Stanley Milgram Quote: “Some system of authority is a requirement of all communal living, and it is only the man dwelling in isolation who is no...”





![Solved 1·Given that x = [1 5 2 8 9 0 1]and y = [5 2 2 6 0 0 | Chegg.com Solved 1·Given that x = [1 5 2 8 9 0 1]and y = [5 2 2 6 0 0 | Chegg.com](https://d2vlcm61l7u1fs.cloudfront.net/media%2F024%2F024532fa-fe1d-4fb8-a18b-938598240c29%2FphpvUjNMe.png)


![NIH STROKE SCALE Interval: 1[ ] Baseline 2[ ] 2 hours ... - Medscape NIH STROKE SCALE Interval: 1[ ] Baseline 2[ ] 2 hours ... - Medscape](https://img.yumpu.com/43645244/1/500x640/nih-stroke-scale-interval-1-baseline-2-2-hours-medscape.jpg)
![Git push force [a Git commands tutorial] | Datree.io Git push force [a Git commands tutorial] | Datree.io](https://assets-global.website-files.com/61c02e339c11997e6926e3d9/61c2e47b4d436d4d1a382d76_5e2a1539b3437be8c9018c2f_cover-git-push-force2.png)